Smart Cubes and WisBlock
Ten years ago I had one of those geek urges: learning to solve Rubik's Cube or Magic Cube. Goal was not to do it fast, just to do it. Back then I managed to memorize the 6-7 algorithms for a novice solver and get in done in less than 5 minutes. Not a world record, I know, still I was pretty happy with the experience.
These last months there has been some hype around the cube in our local school and my younger daughter wanted to learn to do it....

The MikroTik wAP LoRa8 is here
Last week I was at the The Things Conference in Amsterdam with a collegue from TTN Catalunya. You could smell the hype. Most of the big players were there. I had the chance to attend some interesting presentations, talk at the booths with people from PyCom, RAK, WifX or SeeedStudio and meet and devirtualize some people like Gonzalo Casas or Andreas Spiess.
Then there were the workshops. You know, I've done a lot of workshops myself and I know that it is hard (if not impossible) to go through a complete workshop without issues....

Hacking the TTI Indoor Gateway
[Update 2021-08-11] Added information on how to enable the CP2102N on the TTIG thanks to @_pub_feuerrot.
Four years ago The Things Network (TTN) kind of revolutionized the IoT world with their effort to reduce hardware and software costs to implement a commons LoRaWAN network. Their bet was backed on Kickstarter by almost a thousand people with almost 300k€ to help create a low-cost LRaWan gateway (and a platform and end devices too)....

Analyze your antennas using an AAI N1201SA
Following up with the series of affordable RF tools I started with the RF Power Monitor 8000, maybe the N1201SA by Accuracy Agilty (sic?) Instrument (AAI) is one of the most exciting devices around. The device is sold as “RF Vector Impedanze Analyzer” and, although it's not a full VNA (Vector Network Analyzer), it gives you enough information to profile your antennas and, according to some reviews, it's so accurate it can compete with professional equipment....
![]()
Grove AI Hat, edge computing in your hands
The industry has been talking about edge computing for some time now. The idea is to distribute the data storage and intelligence in locations closer to where they are needed and only use external services when absolutely necessary. Centralized cloud services have a series of drawbacks for the IIoT world, being maybe latency and security the bigger ones. Some (a lot of?) companies do not want their data to go outside their facilities and critical systems cannot rely on Internet connection....
![]()
RF power monitoring tools on the cheap
Recently we at @ttncat had to prepare a crash course on LoRa, LoRaWAN and The Things Network for a professional school in Barcelona. It was a 15 hours course that covered from the very basics to some more advanced topics on RF like link budget, attenuation or impedance matching. It was fun to go back to my years at college and revisit and update some of those topics. And at the same time it was a great opportunity to upgrade my toolbox....
![]()
Automated unit testing in the metal
Unit testing your code is peace of mind. It has two main direct benefits that impact on your confidence about the code you are writing:
Testing expected behaviors Avoiding regressions (i.e. breaking something that was working fine before) Unit testing embedded systems is a bit more involved since there is the additional constraint of the hardware itself, sometimes more than one device or even different platforms. Quitting (or not even thinking about it) is the easy answer to the problem....
![]()
Monitor your TTN gateways with Node-RED
This time I'd like to write a quick post about a small project we've been working on at the The Things Network** community in Barcelona** (@ttncat). We were worried about the monitoring of the gateways we have deployed, both as a community but also as individuals. Some of our partners have also deployed their own gateways and they are part of the community.
The TTNCat gateway at Vista Rica in Barcelona So how do we get (almost) real-time notifications of incidences in the local TTN network?...
![]()
WhiteCat ESP32 N1
I do not do reviews usually, but I sometimes do exceptions. In this case, it's worth doing it, due to 4 main reasons:
It's a software & hardware open source project It's local (local to me, that's it) It's led by two good friends It's related to LoRa and The Things Network It's awesome! OK, they were actually 5 reasons, but the last one just slipped in.
The WhiteCat ESP32 N1 Board The WhiteCat ESP32 N1 Board is a green board in a long-ish form factor, longer than the LoPy or the Chinese ESP32-based LoRa boards....
![]()
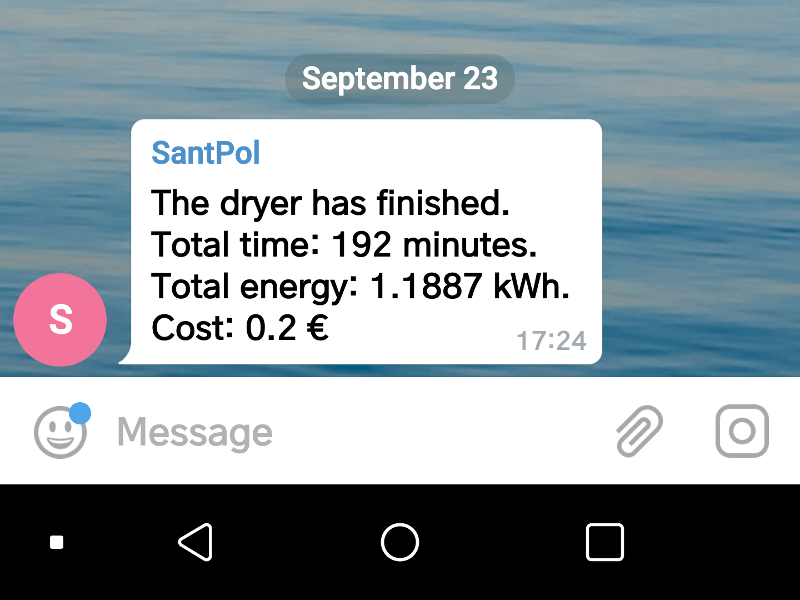
Useful notifications from your home appliances using Node-RED
Some time ago I worked on a home project to get a notification when my washing machine had done its job based on monitoring its power consumption. There was a good reason for that, the machine was outside the house and I had already forgotten about the laundry several times. And when that happens your only option is to wash it again, because it really smells musty…
Monitoring your appliances Use ESPurna :)...